BEYONDTRUST
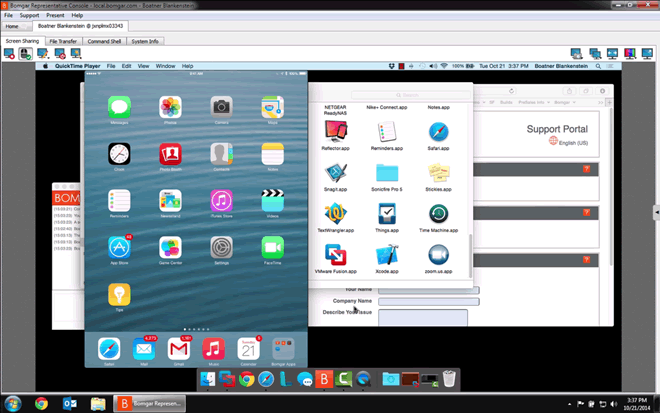
Provide instant, secure, reliable remote support to end-users and customers—on or off your network—using Windows, Mac, iOS, Android, and more. Focus on fixing issues, not fixing connection.
Remote Support Features and Capabilities:
- Chat Support: Enable live support from your website with Clickto-Chat with real-time escalation to screen sharing and remote control, without ever losing contact with the end user.
- Broad Platform Support: Support and provide support from Windows, Mac, Linux, iOS and Android devices. Also support legacy devices using RDP, Telnet, SSH, and VNC.
- Granular Permissions and Roles: Granularly manage teams, users, roles, and session permission settings to enforce a least privilege security posture.
- Collaboration: Resolve support incidents faster by easily collaborating with other technicians and defining escalations paths to skilled resources in a cost-effective manner, while improving customer satisfaction.
- Session Recording and Audit Trail: Track team performance as well as log session activity to serve as an audit trail for security, compliance, and training. • Provide Support from Chrome, Firefox, IE, and More: Our HTML5 Web Rep Console lets you offer secure remote support from any browser – no downloads required – to immediately begin fixing issues from anywhere.
- Integrations: Connect seamlessly with ITSM tools like ServiceNow, third-party authentication solutions like Active Directory, and password managers like BeyondTrust Password Safe.
- Customization & Branding: Maintain corporate branding standards and create trust by customizing your support experience, including chat.
- Deployment: Choose from a physical, virtual, or cloud deployment with flexible licensing options.and a variety of licensing models.
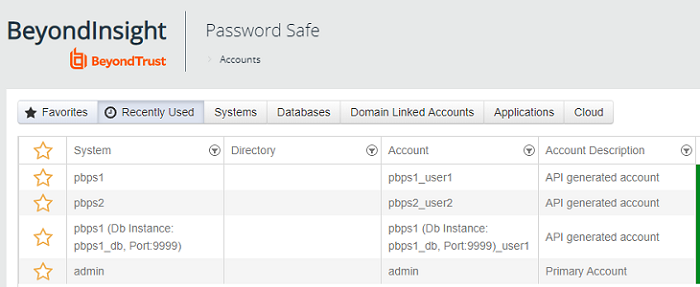
BeyondTrust Password Safe unifies privileged password and privileged session management, providing secure discovery, management, auditing, and monitoring for any privileged credential. Password Safe enables organizations to achieve complete control and accountability over privileged accounts.
Password Safe Features and Capabilities:
- Continuous Automated Account Discovery and Auto-Onboarding: Leverage a distributed network discovery engine to scan, identify, and profile all assets. Dynamic categorization allows autoonboarding into Smart Groups for efficient management.
- Secure SSH Key Management: Automatically rotate SSH keys according to a defined schedule and enforce granular access control and workflow. Leverage private keys to securely log users onto Unix/Linux systems through the proxy, with no user exposure to the key, and with full privileged session recording.
- Application-to-Application Password Management: Eliminate hard-coded or embedded application credentials through an adaptable API interface that includes an unlimited number of Password Caches for scalability and redundancy.
- Enhanced Privileged Session Management: Live session management enables true dual control, enabling admins to record, lock, and document suspicious behavior without killing sessions – or productivity.
- Adaptive Access Control: Evaluate just-in-time context and simplify access requests by considering the day, date, time, and location when a user accesses resources to determine their authorization to access those systems.
- Advanced Privileged Threat Analytics: Measure asset characteristics and user behaviors from one day to the next, assessing the scope and speed of any changes to alert you to suspicious deviations.
BeyondTrust Privilege Management for Desktops elevates privileges to known good applications that require them, controls application usage, and logs and reports on privileged activities using security tools already in place.
Features and Capabilities:
- Least Privilege Enforcement: Elevate privileges to applications for standard users on Windows or MacOS through fine-grained policy-based controls, providing just enough access to complete a task.
- Seamless Application Control: Deliver trust-based application whitelisting with a flexible policy engine to set broad rules. Tailored options enable organizations to choose automatic approval for advanced users – protected by full audit trails – or utilize challenge-response codes. Application whitelisting rules can be applied based on software origin as well.
- Complete Auditing and Reporting: Provide a single, unimpeachable audit trail of all user activity that speeds forensics and simplifies compliance.
- Privileged Threat Analytics: Correlate user behavior against asset vulnerability data and security intelligence from best-of-breed security solutions to provide an overall picture of end-user risk. Integrations with the Security Ecosystem: Built-in connectors to a host of third-party solutions, including help desk applications, vulnerability management scanners, and SIEM tools, ensure that organizations realize a return on their security investments.
- Integrations with the Security Ecosystem: Built-in connectors to a host of third-party solutions, including help desk applications, vulnerability management scanners, and SIEM tools, ensure that organizations realize a return on their security investments.

